Telecom Cabinet Power Controller Monitoring Alerts: Configuration Logic and False Alarm Avoidance of Hierarchical Push (SMS/Email/APP)

A Telecom Cabinet Power Controller enables teams to monitor power events and environmental conditions in real time. Reliable remote monitoring supports proactive maintenance and faster response to faults. Multi-channel notifications—such as SMS, email, and app alerts—deliver critical information to the right personnel. Using hierarchical push logic, organizations can prioritize alerts based on severity. Security protocols and strong configuration management help prevent false alarms and unauthorized access.
Key Takeaways
Telecom Cabinet Power Controllers monitor key parameters like voltage, temperature, humidity, and battery health to detect issues early and keep systems running smoothly.
Setting tiered alert thresholds and using delay timers help prevent false alarms by filtering out brief or minor fluctuations.
Remote monitoring with protocols like SNMP and Modbus enables real-time oversight and faster fault response across multiple sites.
Hierarchical push logic prioritizes alerts by severity and uses escalation rules to ensure critical events reach the right personnel quickly.
Regular sensor maintenance, adaptive thresholds, and strong security practices reduce false alarms and protect the system from unauthorized access.
Telecom Cabinet Power Controller Alerts

Alert Parameters
Telecom Cabinet Power Controller systems monitor a range of critical parameters to ensure reliable operation. These parameters help operators detect issues early and maintain optimal performance. Key alert parameters include:
Voltage: Monitors supply and output voltages to identify fluctuations or drops.
Current: Tracks current draw to prevent overloads and detect abnormal consumption.
Temperature: Measures internal cabinet temperature to avoid overheating.
Battery Performance: Assesses battery voltage and charge/discharge cycles to prevent failures.
Humidity: Detects moisture levels that could damage sensitive electronics.
Door Status and Intrusion: Monitors cabinet access for security breaches.
Real-time monitoring of these parameters allows teams to respond quickly to irregularities such as voltage drops, overheating, or battery degradation. Data logging and analytics further support trend analysis and predictive maintenance, reducing the risk of unexpected failures.
Thresholds and Validation
Setting appropriate thresholds is essential for effective alerting. Telecom Cabinet Power Controller devices use tiered thresholds to distinguish between early warnings and critical events. Operators configure these thresholds based on recommended ranges for each parameter.
Temperature and Humidity: Sensors monitor environmental conditions. For example, a tier-one humidity alert may trigger if levels fall below 40% or rise above 60%. A tier-two critical alert activates below 30% or above 70%.
Voltage: LLVD (Low Line Voltage Disconnect) thresholds protect equipment by disconnecting loads when voltage drops below safe levels. For a 48V system, the LLVD threshold might be set at 40V.
Battery: BLVD (Battery Low Voltage Disconnect) thresholds prevent overdischarge. For a 48V battery, the BLVD threshold could be set at 42V.
Operators place sensors strategically within each cabinet to ensure comprehensive coverage. When thresholds are breached, the system immediately notifies maintenance personnel. This approach enables proactive action, maintains operational efficiency, and protects valuable equipment.
Remote Monitoring
Remote monitoring forms the backbone of modern telecom cabinet management. Telecom Cabinet Power Controller solutions integrate with industry-standard protocols to provide seamless connectivity and real-time oversight. The following table summarizes key aspects of remote monitoring:
Feature/Aspect | Description |
|---|---|
Protocols Supported | SNMP traps/gets, Modbus TCP, BACnet IP, DNP3 |
Devices | Controllers, panels, expansion modules |
Software Platform | Enterprise dashboards with analytics and visualization tools |
Monitoring Capabilities | Power status, environmental conditions, security monitoring |
Integration | Connects with enterprise management systems via SNMP, Modbus, BACnet |
Benefits | Proactive maintenance, reduced downtime, alarm management, multi-site support |
User Interface | Site visualization, alarm tables, heatmaps, and reports |
Use Case | Remote monitoring and control of telecom cabinet power and related equipment |
Modern controllers, such as the AKCP sensorProbe+ series, support BACnet/IP and SNMP natively. This direct integration eliminates the need for additional gateways, reducing complexity and cost. Operators benefit from faster fault detection, improved asset protection, and enhanced operational continuity. Automated alerts and analytics enable predictive maintenance, while robust security measures—such as encryption and access controls—protect sensitive data during remote monitoring.
Integration with remote monitoring protocols also presents challenges. Teams must address compatibility issues, manage different communication standards, and ensure secure, reliable channels. Regular calibration and firmware updates help maintain sensor accuracy and system reliability.
Hierarchical Push Logic

Severity Levels
Operators assign severity levels to alerts based on a combination of risk factors and operational impact. The Telecom Cabinet Power Controller evaluates each event using criteria such as violation nature, risk to system reliability, and the presence of monitoring systems. Severity levels help teams prioritize responses and allocate resources efficiently.
Criteria/Factor | Description/Example |
|---|---|
Violation Nature | Failure to control access points, incomplete risk assessments, procedural lapses |
Risk to Bulk Power System Reliability | Serious, moderate, minimal, or no substantial risk based on event specifics and system impact |
Duration and Frequency | Single-day incidents versus ongoing or repeated violations |
Monitoring and Alarm Systems | Presence or absence of alarms, continuous monitoring, and human observation |
Unauthorized Access Attempts | Whether unauthorized access occurred or was attempted |
Aggravating Factors | Repeat violations, noncompliance, concealment attempts |
Mitigating Factors | Self-reporting, cooperation, compliance programs |
Severity Levels Assigned | Medium, Lower, High, or N/A depending on risk and control effectiveness |
Severity levels—such as High, Medium, or Lower—guide the escalation process and ensure that critical events receive immediate attention. Operators rely on these levels to distinguish between routine maintenance alerts and incidents that threaten system reliability.
Notification Channels
Telecom Cabinet Power Controller systems use multiple notification channels to deliver alerts to the right personnel. Each channel offers distinct advantages for speed, reliability, and accessibility. The following table summarizes the technical requirements and features of common notification methods:
Feature/Requirement | Details |
|---|---|
Email Notifications | Supports SMTP authentication with SSL security; up to 8 recipients; email-to-SMS gateway supported |
SMS Integration | Indirect via email-to-SMS; direct SMS integration not available |
App Notifications | Not explicitly supported |
Network Connectivity | Ethernet 10/100 BaseT; TCP/IP protocols including DHCP and static IP addressing |
Alarm Notification Methods | Audible alarm, visible LED, email, SNMP traps, relay outputs |
SNMP Support | SNMP v1 and v2c traps for network management system integration |
Web Interface | Password protected, mobile-friendly, no additional software needed for configuration |
Relay Outputs | 1 Form C summary relay output for external device control |
Protocols | TCP/IP, SMTP, SNMP, Modbus TCP/IP |
Security | SMTP authentication, SSLv3 RSA encryption, web interface password protection |
Integration with BMS | Modbus TCP/IP support for building management system integration |
Timekeeping | Onboard RTC and NTP capable (requires internet) |
Additional Notes | No direct app notification or SMS module; relies on email-to-SMS gateways |
Operators configure notification channels to match organizational needs. Email notifications provide detailed event logs and support secure transmission. SMS alerts, delivered via email-to-SMS gateways, reach field technicians quickly. SNMP traps integrate with network management systems for centralized oversight. Audible alarms and LEDs offer immediate local feedback.
Escalation Rules
Escalation rules define how alerts move through the notification hierarchy based on severity and response time. The Telecom Cabinet Power Controller uses these rules to ensure that unresolved or critical events receive prompt attention from higher-level personnel.
The system sends initial alerts to on-site technicians for low and medium severity events.
If technicians do not acknowledge or resolve the issue within a set timeframe, the system escalates the alert to supervisors via email or SNMP.
For high-severity incidents, the system notifies management and network operations centers immediately, bypassing lower tiers.
Automated escalation ensures that critical events never go unnoticed, even during off-hours or staff shortages.
Escalation rules reduce the risk of missed alerts and improve response efficiency. Operators can customize escalation paths to fit organizational structures and operational priorities.
Reducing Alert Fatigue and Improving Response Efficiency
Modern monitoring platforms address alert fatigue by centralizing management and customizing thresholds. Operators use dashboards to aggregate sensor data from multiple sites, focusing on critical incidents and minimizing unnecessary alerts. Predictive analytics and AI forecast equipment failures, enabling proactive maintenance and reducing manual alert handling. IoT automation supports continuous monitoring and automated responses, lowering emergency visits and maintenance costs. Network Operations Centers coordinate monitoring with standardized processes, preventing staff burnout and ensuring effective alert management.
Centralized dashboards unify access to key metrics and streamline communication.
Predictive maintenance schedules interventions before failures occur.
AI and machine learning automate responses and filter non-critical alerts.
IoT solutions enable continuous monitoring and automated control actions.
Operators benefit from reduced alert fatigue, faster response times, and improved system reliability. The hierarchical push logic ensures that every alert reaches the appropriate personnel, while advanced analytics and automation optimize operational efficiency.
False Alarm Avoidance
Filtering Techniques
Operators use several filtering techniques to minimize false alarms in telecom cabinet monitoring systems. These methods improve reliability and reduce unnecessary maintenance calls.
Select sensors designed for telecom environments, such as photoelectric smoke detectors.
Test and calibrate sensors every month to maintain accuracy.
Clean sensors annually to prevent dust buildup.
Install sensors away from airflow, humid, or dusty locations to avoid false triggers.
Replace batteries every 6 to 12 months and test them monthly.
Adjust alarm sensitivity based on site-specific environmental data.
Schedule routine maintenance for cleaning and inspection.
Troubleshoot false alarms by checking environmental factors and adjusting sensitivity.
Verify wiring and network connections regularly for secure integration.
Operators often combine multiple sensor types and integrate intelligent control systems. Real-time monitoring and AI-driven anomaly detection further enhance alarm accuracy and reduce false positives.
Tip: Regular sensor maintenance and strategic placement help prevent nuisance alarms and ensure reliable system performance.
Delay Timers
Delay timers play a crucial role in avoiding false alarms caused by transient events. Operators configure delay timers to require a parameter to remain outside its threshold for a set period before triggering an alert. For example, a temperature sensor may need to detect high readings for 60 seconds before sending a notification. This approach filters out brief spikes and prevents unnecessary alerts.
Parameter | Typical Delay Timer | Purpose |
|---|---|---|
Temperature | 30–60 seconds | Avoid alerts from short spikes |
Humidity | 30 seconds | Filter out rapid fluctuations |
Door Status | 10 seconds | Prevent false intrusion alerts |
Delay timers help teams focus on genuine issues and reduce the risk of alert fatigue.
Adaptive Thresholds
Adaptive thresholds allow systems to adjust alert levels based on historical data and changing conditions. Operators analyze baseline environmental data unique to each site and set thresholds that reflect normal fluctuations. Intelligent control systems use machine learning to refine these thresholds over time, responding to seasonal changes or equipment upgrades.
Adaptive thresholds reduce false alarms by accounting for site-specific patterns. Operators benefit from fewer nuisance alerts and improved detection of real problems.
Note: Adaptive thresholds require regular review and adjustment to remain effective as site conditions evolve.
Configuration Management
Change Control
Effective change control ensures that configuration updates do not disrupt operations or compromise system reliability. Organizations implement structured processes to track, review, and authorize changes to monitoring parameters, thresholds, and notification rules. Teams document each modification, including the reason, date, and personnel involved. This approach reduces the risk of accidental misconfiguration and supports rapid troubleshooting.
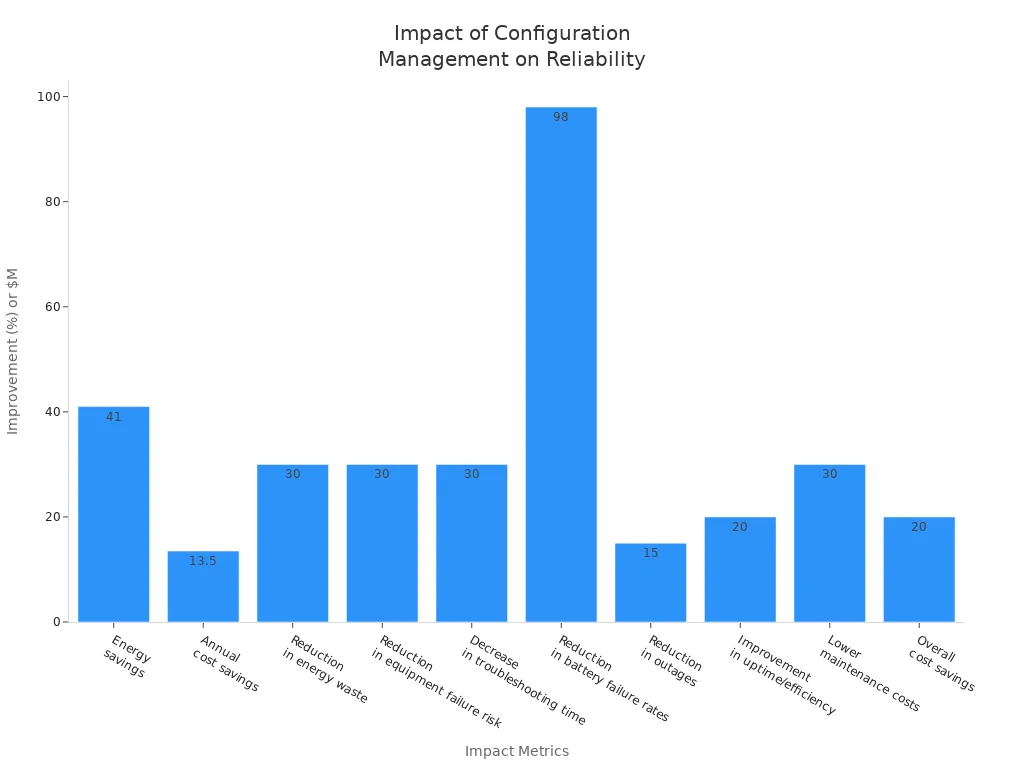
Organization / Company | Impact / Result | Explanation |
|---|---|---|
IBM | Real-time monitoring of power distribution units (PDUs) reduced energy consumption in data centers, enhancing operational stability. | |
U.S. General Services Administration | 41% energy savings, $13.5M annual cost savings | Smart PDUs improved efficiency and financial outcomes, supporting system reliability. |
New York City Underground Power Network | Enhanced reliability | Advanced PDUs prevented power failures in critical infrastructure, reducing downtime. |
Vertiv (Fiji deployment) | Maintained IT and data center availability | ESTEL PDUs ensured telecom operations continued during outages, improving network uptime. |
GUDE | Up to 30% reduction in energy waste | Measurement and monitoring capabilities supported sustainable energy use and reliability. |
Change control practices deliver measurable benefits. Real-time monitoring and centralized dashboards reduce troubleshooting time by 30%. Predictive maintenance and early anomaly detection lower equipment failure risk by up to 30%. These improvements lead to fewer outages and higher operational efficiency.
Security and Access
Security protocols protect critical infrastructure from unauthorized access and environmental threats. Organizations deploy secure locking mechanisms, such as electronic or combination locks, and use reinforced materials to resist tampering. Advanced access control systems, including keycard and biometric readers, restrict entry to authorized personnel only. Remote monitoring tools provide real-time alerts and maintain detailed access logs for oversight.
Physical safety measures, such as weatherproof seals and fire-resistant coatings, shield equipment from environmental hazards. Compliance with industry standards like NEMA and IP ratings ensures cabinets withstand harsh conditions and maintain operational reliability.
Tip: Regularly update access permissions and review security logs to maintain a robust defense against both physical and cyber threats.
Alarm Presets
Alarm presets streamline the configuration process and ensure consistency across multiple sites. Operators select from predefined templates for common scenarios, such as temperature, humidity, or voltage anomalies. These presets reflect best practices and industry standards, reducing setup time and minimizing errors.
Presets enable rapid deployment of new cabinets.
Standardized thresholds support uniform response protocols.
Templates simplify training for new personnel.
Centralized dashboards allow teams to manage and update alarm presets remotely. This flexibility supports large-scale operations and ensures that all sites maintain optimal alert settings.
A well-configured Telecom Cabinet Power Controller alert system supports operational reliability and rapid response. Teams should:
Use AI-driven monitoring and multiple sensor types for accurate, real-time alerts.
Adapt alert systems with intelligent PDUs and modular designs to meet changing needs.
Integrate strong encryption, programmable access, and regular protocol updates for robust security.
Regular review, testing, and adaptation ensure the system remains effective and resilient.
FAQ
What protocols do telecom cabinet power controllers support for remote monitoring?
Most controllers support SNMP, Modbus TCP, and BACnet IP. These protocols enable integration with enterprise management systems. Operators can monitor power, environment, and security data in real time.
How can teams reduce false alarms in telecom cabinet monitoring?
Teams use sensor calibration, delay timers, and adaptive thresholds. Regular maintenance and strategic sensor placement also help. These practices minimize nuisance alerts and improve system reliability.
Who receives alerts when a critical event occurs?
The system sends high-severity alerts directly to supervisors or network operations centers. Lower-severity events notify on-site technicians first. Escalation rules ensure unresolved issues reach higher-level personnel.
What security measures protect telecom cabinet alert systems?
Operators use password-protected web interfaces, SSL encryption, and access control systems. Physical security includes electronic locks and reinforced cabinets. Regular reviews of permissions and logs strengthen defense against unauthorized access.
CALL US DIRECTLY
86-13752765943
3A-8, SHUIWAN 1979 SQUARE (PHASE II), NO.111, TAIZI ROAD,SHUIWAN COMMUNITY, ZHAOSHANG STREET, NANSHAN DISTRICT, SHENZHEN, GUANGDONG, CHINA

